Integrated Windows Authentication Iwa With Kerberos And Wso2 Identity Server By Farasath Ahamed Identity Beyond Borders Medium
Hbase Security Kerberos Authentication Authorization Dataflair
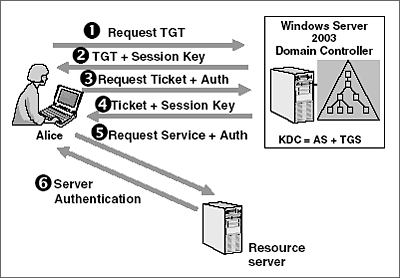
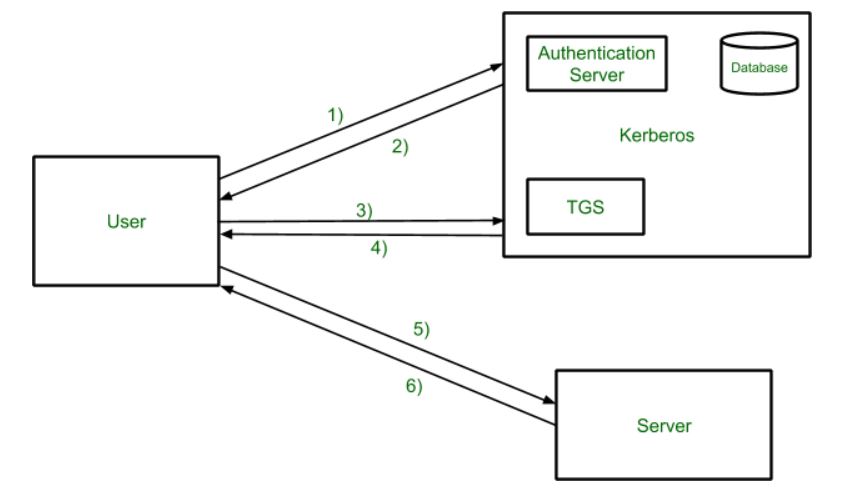
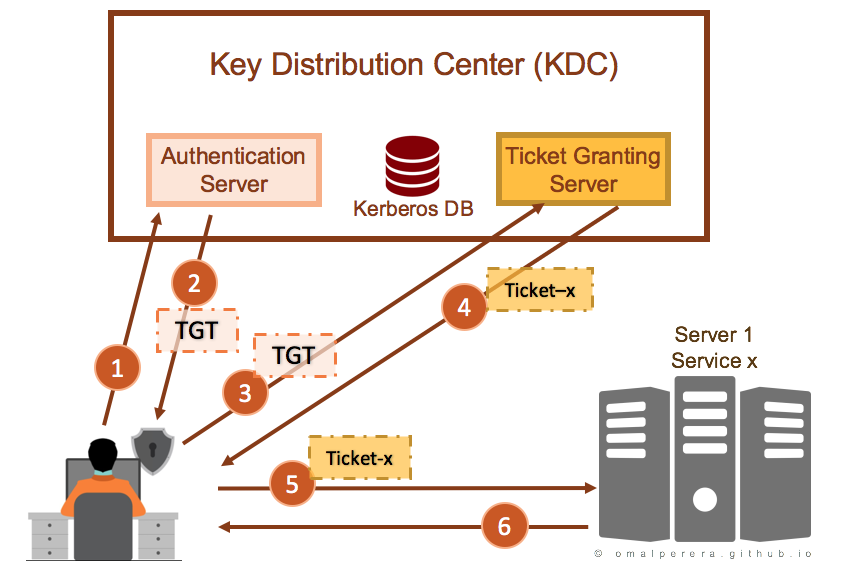
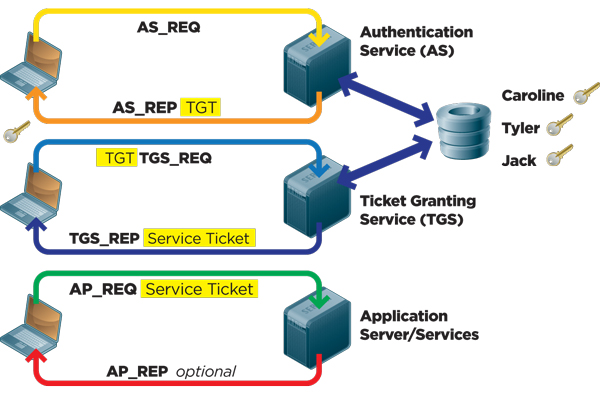
Five Steps To Using The Kerberos Protocol
Understanding Kerberos Double Hop Microsoft Tech Community

Diagrammatic Explanation Of Kerberos Authentication Balaji Gopal
Kerberos Authentication 101 Understanding The Essentials Of The Kerberos Security Protocol Redmondmag Com
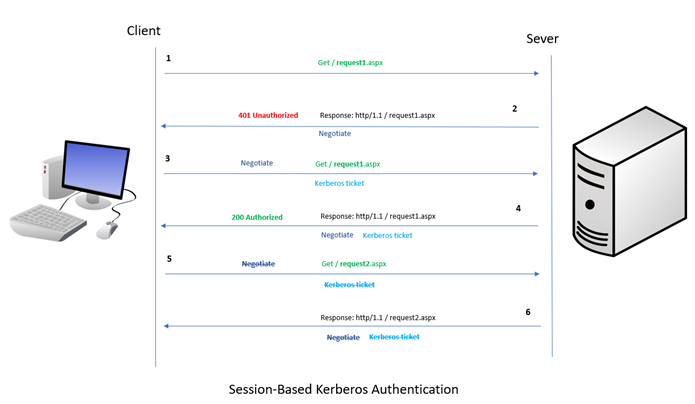
Request Based Versus Session Based Kerberos Authentication Or The Authpersistnonntlm Parameter Microsoft Tech Community
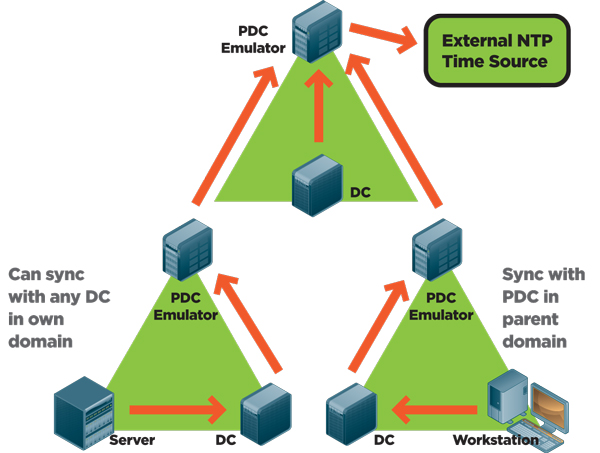
Kerberos Authentication 101 Understanding The Essentials Of The Kerberos Security Protocol Redmondmag Com
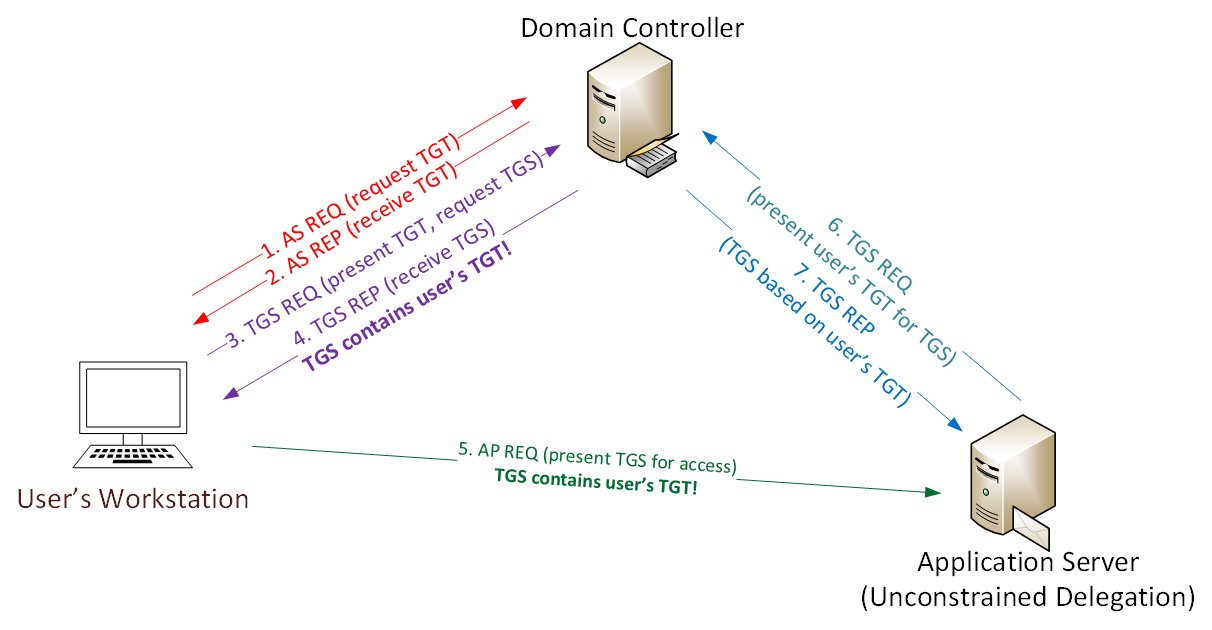
Active Directory Security Risk 101 Kerberos Unconstrained Delegation Or How Compromise Of A Single Server Can Compromise The Domain Active Directory Security
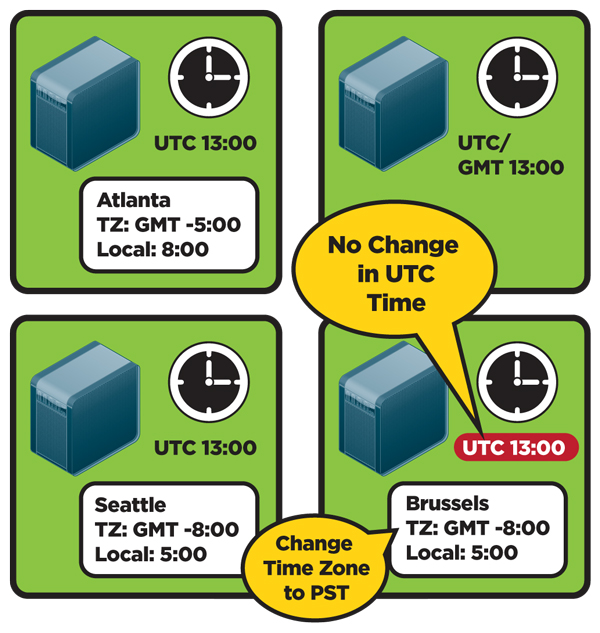
Kerberos Authentication 101 Understanding The Essentials Of The Kerberos Security Protocol Redmondmag Com
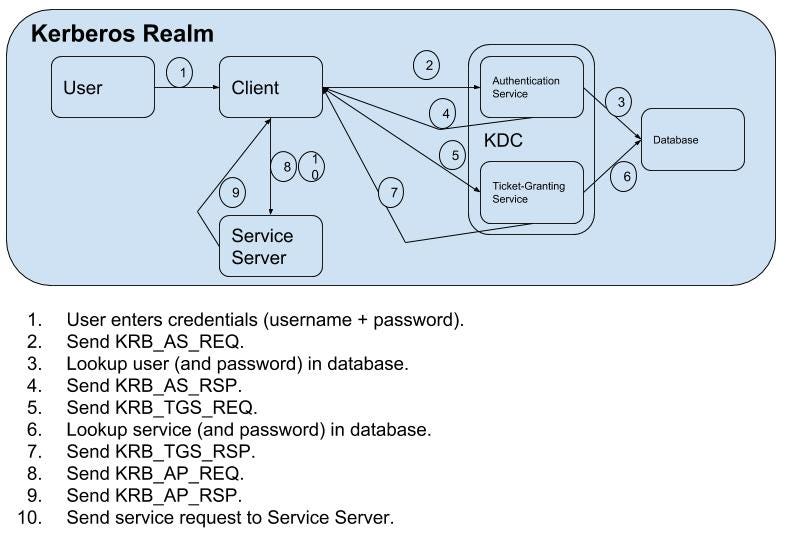
Kerberos And Windows Security Kerberos On Windows By Robert Broeckelmann Medium

Kerberos Protocol Question Sysadmin
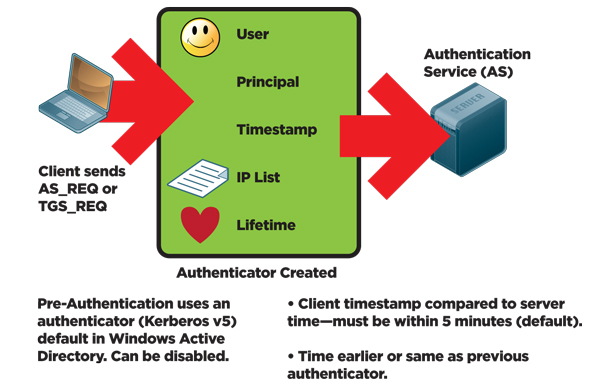
Kerberos Authentication 101 Understanding The Essentials Of The Kerberos Security Protocol Redmondmag Com